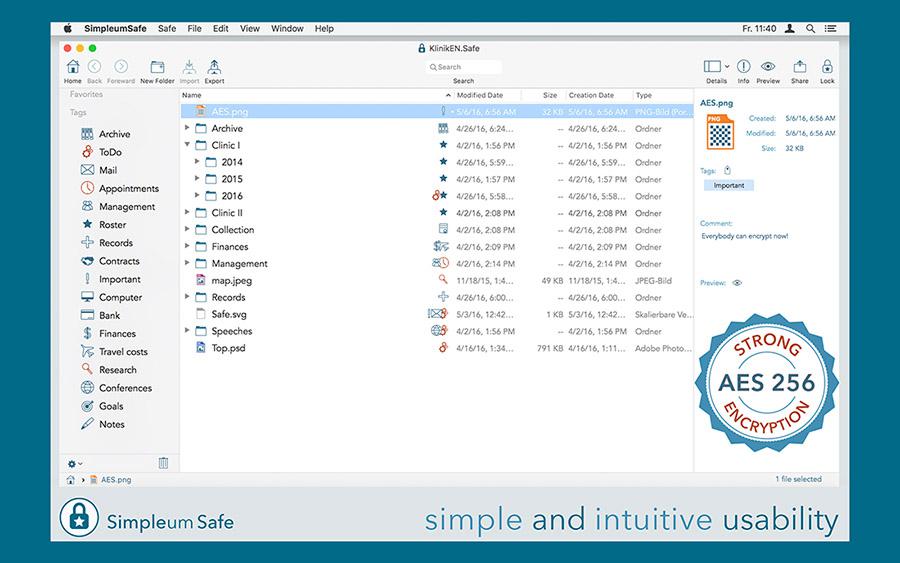
SimpleumSafe
SimpleumSafe is a suitable technical solution for the protection of digital personal data according to GDPR for Mac, iPhone and iPad. Encrypto offers fast, cross-platform encryption to help protect sensitive files before they’re sent or uploaded through the internet. It’s unobtrusive, easy to use, and best of all, absolutely free.
This is an effective tutorial that helps you learn how to remove SimpleumSafe on your macOS and Mac OS X. This tutorial contains an automatically removal solution, a manually removal solution and a video is provided which teach you how to remove SimpleumSafe by MacRemover.
What is it?
SimpleumSafe is a Microsoft Windows compatibility layer available for Linux, macOS, and Chrome OS. This compatibility layer enables many Windows-based applications to run on Linux operating systems, macOS, or Chrome OS. SimpleumSafe is developed by CodeWeavers and based on Wine, an open-source Windows compatibility layer.
Video: How To Automatically Remove SimpleumSafe by MacRemover?
Use automatically removal solution to remove SimpleumSafe in your macOS
1. Download and install MacRemover
2. Switch to Finder and select Go -> Applications from the Finder menu.
3. Locate the MacRemover icon and double-click on it.
4. SimpleumSafe icon will be displayed on the Apps listview of MacRemover, and click on it.

5. Click “Run Analysis”, and then “Complete Uninstall”. SimpleumSafe will be automatically and completely removed.
Use manually removal solution to remove SimpleumSafe in your macOS
The steps listed below will guide you in removing SimpleumSafe:
1. Switch to the Finder and select Go -> Utilities from the Finder Wd my passport for mac 3tb. menu.
2. Locate the Activity Monitor icon and double-click on it.
3. On the main window of Activity Monitor, find the entry for SimpleumSafe, Autoupdate, fileop, SimpleumSafeTrialSell, SimpleumSafeOSXShareExtension select them and click Quit Process.

4. Switch to the Finder again and select Go -> Applications from the Finder menu. Find the SimpleumSafe icon, right-click on it and select Move to Trash. if user password is required, enter it.
5.Then, hold an Option key while the Finder’s Go is being selected. Select Library. Locate any folders that are named the following names and drag them to the Trash.
- com.simpleum.safe.mac (in Application Support folder)
- com.crashlytics (in Application Support folder)
- com.crashlytics.data (in Caches folder)
- com.simpleum.safe.mac (in Caches folder)
- *.group.com.simpleum.safe (in Group Containers folder)
6. The following files/folders of SimpleumSafe, you need to use “rm” command to delete on the Terminal.

- SimpleumSafe.app
- com.simpleum.safe.mac.plist
7. Restart your macOS.
As part of my book's chapter on end-to-end encryption I've been writing about the horrors of PGP.
Simpleumsafe Review
As a recap of what's bad with PGP:
- No authenticated encryption. This is my biggest issue with PGP personally.
- Receiving a signed message means nothing about who sent it to you (see picture below).
- Usability issues with GnuPG (the main implementation).
- Discoverability of public keys issue.
- Bad integration with emails.
- No forward secrecy.
For more, see my post on a history of end-to-end encryption and the death of PGP.
(excerpt from the book Real World Cryptography)
Simpleumsafe Icloud
The latter two I don't care that much. Integration with email is doomed from my point of view. And there's just not way to have forward secrecy if we want a near-stateless system.
Email is insecure. Even with PGP, it’s default-plaintext, which means that even if you do everything right, some totally reasonable person you mail, doing totally reasonable things, will invariably CC the quoted plaintext of your encrypted message to someone else (we don’t know a PGP email user who hasn’t seen this happen). PGP email is forward-insecure. Email metadata, including the subject (which is literally message content), are always plaintext. (Thomas Ptatcek)
Simpleumsafe Backup
OK so what can I advise to my readers? What are the alternatives out there?
For file signing, Frank Denis wrote minisign which looks great.
For file encryption, I wrote eureka which does the job.There's also magic wormhole which is often mentioned, and does some really interesting cryptography, but does not seem to address a real use-case (in my opinion) for the following reason: it's synchronous. We already have a multitude of asynchronous ways to transfer files nowadays (dropbox, google drive, email, messaging, etc.) so the problem is not there. Actually there's really no problem.. we just all need to agree on one way of encrypting a file and eureka does just that in a hundred lines of code.
Simpleumsafe Synchronisieren
(There is a use-case for synchronous file transfer though, and that's when we're near by. Apple's airdrop is for that.)
For one-time authenticated messaging (some people call that signcryption) which is pretty much the whole use-case of PGP, there seems to be only one contender so far: saltpack. The format looks pretty great and seems to address all the issues that PGP had (except for forward secrecy, but again I don't consider this a deal breaker). It seems to only have two serious implementations: keybase and keys.pub. Keybase a bit more involved, and keys.pub is dead simple and super well put.Note that age and rage (which are excellent engineering work) seem to try to address this use case. Unfortunately they do not provide signing as Adam Caudill pointed out. Let's keep a close eye on these tools though as they might evolve in the right direction.To obtain public keys, the web of trust (signing other people keys) hasn't been proven to really scale, instead we are now in a different key distribution model where people broadcast their public keys on various social networks in order to instill their identity to a specific public key. I don't think there's a name for it.. but I like to call it broadcast of trust.
For encrypted communications, Signal has clearly succeeded as a proprietary solution, but everyone can benefit from it by using other messaging apps like WhatsApp and Wire or even federated protocols like Matrix. Typing softwares for mac. Matrix' main implementation seems to be Riot which I've been using and really digging so far. It also looks like the French government agrees with me.Same thing here, the web of trust doesn't seem to work, and instead what seems to be working is relying on centralized key distribution servers and TOFU but verify (trust the first public key you see, but check the fingerprint out-of-band later).
